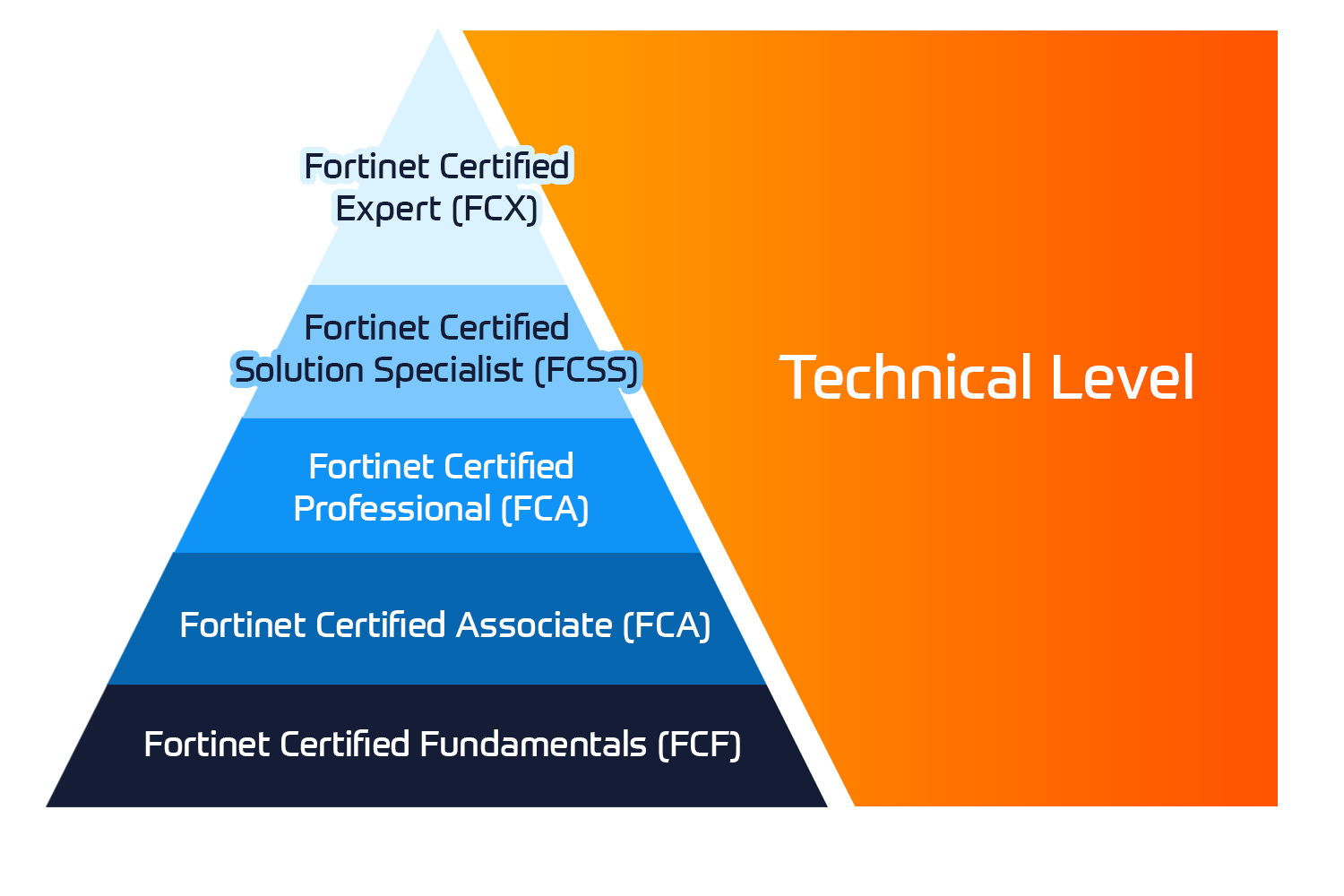
Palo Alto Networks® Traps™ Advanced Endpoint Protection prevents sophisticated vulnerability exploits and unknown malware-driven attacks. Successful completion of this two-day, instructor-led course equips the student to deploy Traps in large-scale or complex configurations and optimize its configuration.
Ota yhteyttä
Voit olla meihin yhteydessä ja tiedustella koulutuksistamme täydentämällä yhteystietosi ja koulutuksen nimen oheen.
 Kesto
Kesto 2 päivää
 Toimitus
Toimitus (Online ja paikan päällä)
 Hinta
HintaHinta pyydettäessä
Students will learn how to design, build, implement, and optimize large scale Traps deployments: those with multiple servers and/or thousands of endpoints. In hands-on lab exercises, students will distribute Traps endpoint software in an automated way; prepare master images for VDI deployment; build multi-ESM deployments; design and implement customized policies; test Traps with exploits created using Metasploit; and examine prevention dumps with windbg.
Module 1: Deploying Traps
- Distributing endpoint software
- TLS/SSL options
- Virtual Desktop Infrastructure (VDI) deployment
- External logging and SIEM integration
Module 2: Scaling Traps Deployments Up
- Role-based Access Control
- Deployment patterns, including Multi-ESM Server deployment
- Migration tasks
Module 3: Optimizing Traps
- Optimizing server settings
- Defining conditions
- Designing optimized policies
- Implementing ongoing maintenance
Module 4: Advanced Traps Forensics
- Agent queries
- Resources for malicious software testing
- Exploit challenge testing with Metasploit
- Exploit dump analysis with windbg
Module 5: Advanced Traps Troubleshooting
- Endpoint Security Manager and Traps architecture
- Troubleshooting scenarios using dbconfig and cytool
- Troubleshooting application compatibility
- Troubleshooting BITS connectivity
- Security Engineers, System Administrators, and Technical Support Engineers
- Students should have completed “Traps: Install, Configure, and Manage” or (for Palo Alto Networks employee and partner SEs) “PSE: Endpoint Associate” training. Windows system administration skills and familiarity with enterprise security concepts also are required.
Palo Alto Networks® Traps™ Advanced Endpoint Protection prevents sophisticated vulnerability exploits and unknown malware-driven attacks. Successful completion of this two-day, instructor-led course equips the student to deploy Traps in large-scale or complex configurations and optimize its configuration.
Students will learn how to design, build, implement, and optimize large scale Traps deployments: those with multiple servers and/or thousands of endpoints. In hands-on lab exercises, students will distribute Traps endpoint software in an automated way; prepare master images for VDI deployment; build multi-ESM deployments; design and implement customized policies; test Traps with exploits created using Metasploit; and examine prevention dumps with windbg.
Module 1: Deploying Traps
- Distributing endpoint software
- TLS/SSL options
- Virtual Desktop Infrastructure (VDI) deployment
- External logging and SIEM integration
Module 2: Scaling Traps Deployments Up
- Role-based Access Control
- Deployment patterns, including Multi-ESM Server deployment
- Migration tasks
Module 3: Optimizing Traps
- Optimizing server settings
- Defining conditions
- Designing optimized policies
- Implementing ongoing maintenance
Module 4: Advanced Traps Forensics
- Agent queries
- Resources for malicious software testing
- Exploit challenge testing with Metasploit
- Exploit dump analysis with windbg
Module 5: Advanced Traps Troubleshooting
- Endpoint Security Manager and Traps architecture
- Troubleshooting scenarios using dbconfig and cytool
- Troubleshooting application compatibility
- Troubleshooting BITS connectivity
- Security Engineers, System Administrators, and Technical Support Engineers
- Students should have completed “Traps: Install, Configure, and Manage” or (for Palo Alto Networks employee and partner SEs) “PSE: Endpoint Associate” training. Windows system administration skills and familiarity with enterprise security concepts also are required.
- ` Päivämäärä pyynnöstä

 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Sweden
Sweden Italy
Italy Netherlands
Netherlands Norway
Norway