This course prepares Trellix SIEM engineers and analysts to understand, communicate, and use the features provided by Trellix Enterprise Security Manager. Through hands-on lab exercises, you will learn how to optimize the Enterprise Security Manager by using Trellix recommended best practices and methodologies.
Ota yhteyttä
Voit olla meihin yhteydessä ja tiedustella koulutuksistamme täydentämällä yhteystietosi ja koulutuksen nimen oheen.
 Kesto
Kesto 4 päivää
 Toimitus
Toimitus (Online ja paikan päällä)
 Hinta
HintaHinta pyydettäessä
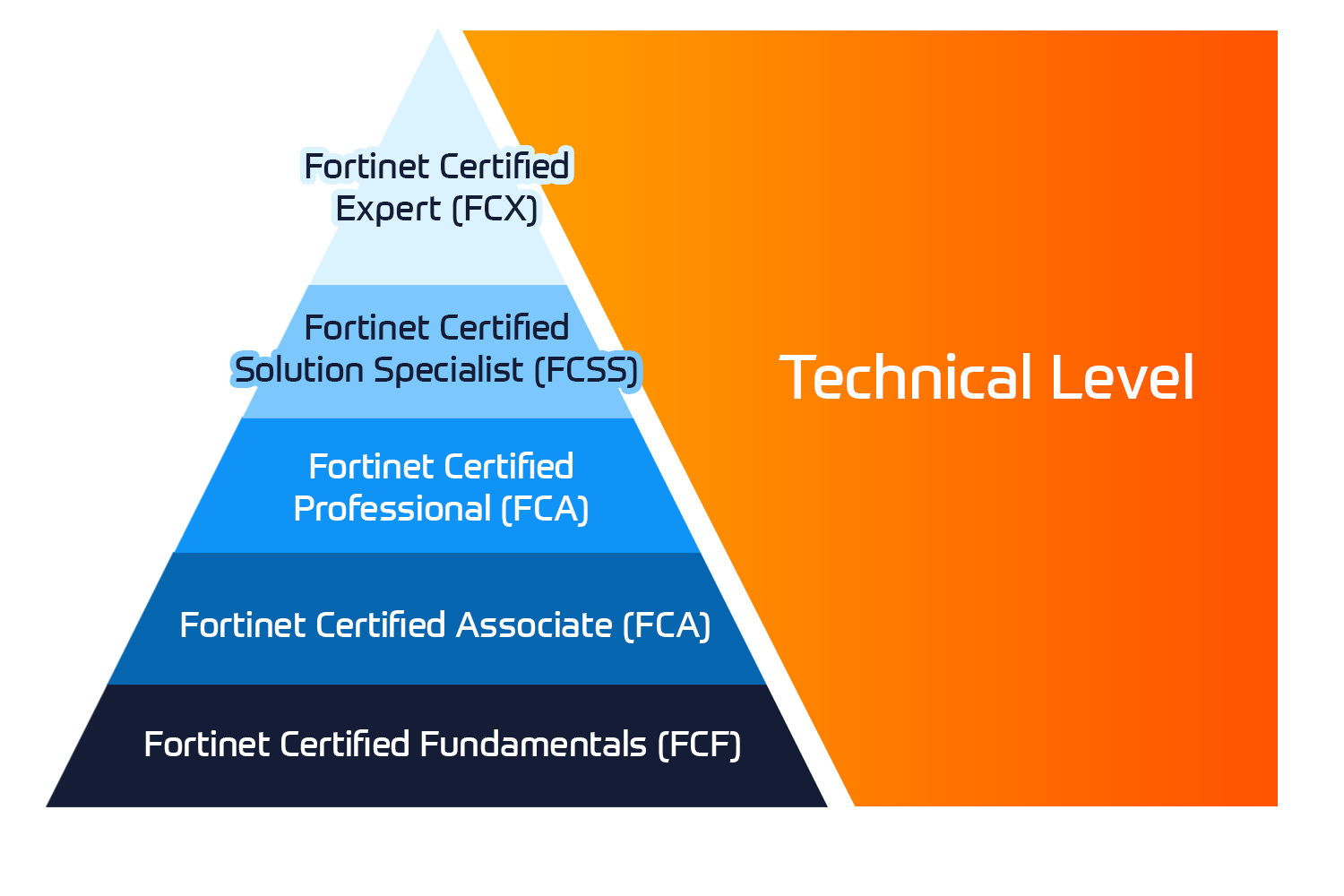
- Define Trellix SIEM concepts, identify appliances, and describe the SIEM solution component architecture
- Navigate and configure the features provided in this release
- Add, import, and configure data sources
- Navigate Enterprise Log Manager (ELM) and configure settings and data storage
- Navigate Enterprise Log Search (ELS) and configure settings and searches
- Navigate the ESM UI dashboard and create custom ESM data views
- Locate events, filter data, and manage cases
- Modify default aggregation of events and flows to meet company requirements
- Navigate and configure the Policy Editor to closely reflect your actual environment
- Use correlation to identify events of interest, isolate correlated events, then modify the rule to suit requirements
- Create and configure watchlists and alarms
- Create and configure reports
- Perform routine maintenance on ESM, including updates and clearing policy modifications and rule updates
- Perform basic ESM product troubleshooting
- Describe High Availability and Disaster Recovery configuration techniques and design
- Practice using the ESM dashboards and views using real-world examples
Day 1:
- Welcome
- Architecture Overview
- Devices and Settings
- ESM User Interface and Views
Day 2:
- Data Sources
- Working with the ELM and ELS
- Event Analysis
- Aggregation
Day 3:
- Watchlists and Policy Editor
- Query Filters
- Rule Correlation
- Alarms
Day 4:
- Workflow and Analysis
- Reports
- System Maintenance and Troubleshooting
- Introduction to Use Case Design
This course is intended for Enterprise Security Manager users responsible for monitoring activity on systems, networks, databases, applications, and for configuration and management of the Enterprise Security Manager solution.
Students taking this course should have a working knowledge of networking and system administration concepts, a good understanding of computer security concepts, and a general understanding of networking and application software.
This course prepares Trellix SIEM engineers and analysts to understand, communicate, and use the features provided by Trellix Enterprise Security Manager. Through hands-on lab exercises, you will learn how to optimize the Enterprise Security Manager by using Trellix recommended best practices and methodologies.
- Define Trellix SIEM concepts, identify appliances, and describe the SIEM solution component architecture
- Navigate and configure the features provided in this release
- Add, import, and configure data sources
- Navigate Enterprise Log Manager (ELM) and configure settings and data storage
- Navigate Enterprise Log Search (ELS) and configure settings and searches
- Navigate the ESM UI dashboard and create custom ESM data views
- Locate events, filter data, and manage cases
- Modify default aggregation of events and flows to meet company requirements
- Navigate and configure the Policy Editor to closely reflect your actual environment
- Use correlation to identify events of interest, isolate correlated events, then modify the rule to suit requirements
- Create and configure watchlists and alarms
- Create and configure reports
- Perform routine maintenance on ESM, including updates and clearing policy modifications and rule updates
- Perform basic ESM product troubleshooting
- Describe High Availability and Disaster Recovery configuration techniques and design
- Practice using the ESM dashboards and views using real-world examples
Day 1:
- Welcome
- Architecture Overview
- Devices and Settings
- ESM User Interface and Views
Day 2:
- Data Sources
- Working with the ELM and ELS
- Event Analysis
- Aggregation
Day 3:
- Watchlists and Policy Editor
- Query Filters
- Rule Correlation
- Alarms
Day 4:
- Workflow and Analysis
- Reports
- System Maintenance and Troubleshooting
- Introduction to Use Case Design
This course is intended for Enterprise Security Manager users responsible for monitoring activity on systems, networks, databases, applications, and for configuration and management of the Enterprise Security Manager solution.
Students taking this course should have a working knowledge of networking and system administration concepts, a good understanding of computer security concepts, and a general understanding of networking and application software.
- ` Päivämäärä pyynnöstä

 United Kingdom
United Kingdom Germany
Germany Denmark
Denmark Sweden
Sweden Italy
Italy Netherlands
Netherlands Norway
Norway